The Beginner’s Guide to Network Firewall Security
Would-be busters are capitalizing on modern technology to exploit businesses for financial gain and espionage. Cyber crime is an increasingly prolific and profitable option. It is the single greatest risk to most companies today. If you’re not already aware of the scope of the threat:
- 73% of organizations do not have sufficient network security in place (Hiscox)
- Cyber-attacks have seen a 67% increase since 2014. Malware is the more common attack and the most expensive to resolve. (Accenture)
- Identity theft spikes amid pandemic (WeLiveSecurity)
- Almost half of the cyber attacks in the US were directed at SMBs (CNBC)
- The average cost per cyber attack against an American company in 2018 came out to more than $500,000 (Hiscox)
- The U.S. is predicted to account for more than half of breached data by 2023 (Norton)
The cost of cybercrime comes from business disruption, information loss, revenue loss, and equipment damage. Firewalls are a crucial front line of defense against these threats, but not all firewalls deliver the kind of security at the locations you most need it.
We will explore the different types of network firewalls, explain the different ways to implement firewalls. This will help you select the best solution for your needs.
What is Network Firewall Security?
Network firewall security is a security system used to prevent unauthorized access to a computer while allowing legitimate traffic through. A network firewall monitors and manages incoming and outgoing network traffic. Only data that meets predefined security policies is allowed to pass. This limits unauthorized access to networks and mitigates hackers’ ability to steal customer or proprietary information.
Networking protocols divide data into smaller data packets before transmitting. A network firewall examines these packets to identify anything dangerous to your network.
In addition to protecting your computer from traffic coming into your system, a two-way firewall also protects sensitive data from leaving your computer system. This provides incoming and outgoing protection, sometimes referred to as perimeter protection.
Other types of firewalls exist that provide internal protection, such as web application firewalls. We will only explore network firewalls in this article.
Why Firewalls Matter
A network firewall security system is a key element in network security to help block hackers that seek to gain entry into networks and prevent unauthorized applications from accessing the internet.
Employees can transmit malware unwittingly and unintentionally, which is why it’s important to have a firewall police the content network users access and transfer.
A network firewall is also effective in protecting against viruses and malware, such as keyloggers and Trojan horses, especially when used in conjunction with anti-virus software. They can also help ensure your network and data management practices are compliant with various data security and privacy regulations.
What are the Different Types of Firewalls?
There are several major kinds of network firewalls available today. These include:
- Proxy server
- Packet Filtering
- Stateful Inspection
- Unified Threat Management (UTM)
- Next-Generation Firewalls (NGFWs)
A proxy server acts as a gateway between your computer and the internet, creating a buffer with the webpage you want to visit.
A proxy server can block websites or specific IP addresses, encrypt data so it cannot be read during transmission, and mask or change your IP address.
Packet filtering, also known as stateless inspection, examines and tests each packet that travels through the firewall. Those that meet the filter criteria are allowed to pass through and all others are discarded.
Stateful inspection, also known as dynamic packet filtering, is a newer firewall technology that is considered more secure than packet filtering firewalls.
This technology examines key parts of a packet instead of the contents of each packet. In addition to monitoring this metadata, stateful inspection monitors connections, and only incoming packets that match a known active connection are allowed to pass.
UTM combines a firewall with malware, content filter, intrusion detection, and spam protection into a single package.
NGFWs are the newest firewall technology that inspects packets all the way down to the application level, in addition to packet and protocol filtering.
NGFWs also include deep packet inspection (DPI), an intrusion prevention system (IPS), identity awareness, and stateful inspection. These features allow for advanced protection from malware and persistent threats, which standard firewalls are unable to provide.
Hardware vs. Software Firewalls
While hardware firewalls protect the entire network, software firewalls protect the individual device it is installed on. A hardware firewall protects a network from the outside world and resides between the local network of connected devices and the internet. Software firewalls are installed on each computing device and protect it from internal attacks, such as protecting office computers from a virus that managed to infect a single workstation.
Hardware firewalls are difficult to set up and will most likely require a dedicated IT employee. However, you can manage security for the entire network from one device. Software firewalls are much easier to install, but harder to manage when there are multiple computing devices as maintenance or upgrades must be completed on each computer.
Most companies will need to deploy both hardware and software firewalls, especially if the company deals with sensitive customer information.
On-Premise vs. Cloud Firewalls
Firewalls have been on-premise until the recent emergence of cloud-based firewalls. Locally installed firewalls require some expertise and have a higher upfront cost, but can be customized and personalized in a way that cloud firewalls cannot. On-premise firewalls can also have internal security that cloud firewalls are lacking, such as limiting data traffic between departments or guest and employee networks.
Cloud firewalls can be a good solution for those without a network security specialist or those wanting a subscription-based operational expense, versus the upfront capital expense. Cloud firewalls can sometimes have lag time issues if multiple customers are sharing a resource at the same time.
Application Vs Network Level Firewalls
The most important difference between these types of firewalls is the level where they operate. Those unfamiliar with network security should know there are 7 of these distinct levels, where protection can be offered. Think of these as the areas of vulnerability.
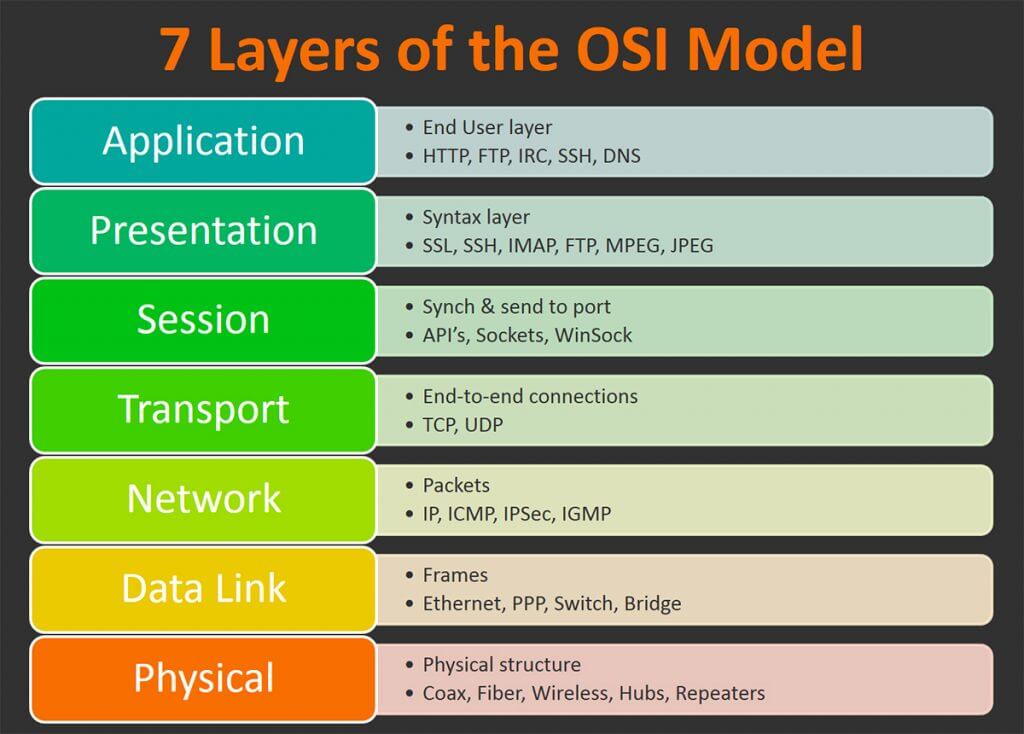
As people spend their careers studying these differences, it is important not to get bogged down here. The main thing to know is that web application firewalls (WAF) operate on layer 7, whereas network firewalls work on 3 and 4.
Practically, this makes network firewalls more common for digital protection for businesses. They are well-suited to protecting against network attacks. These attacks can come from LAN systems, and can move between connected devices.
To learn more about the differences between these, check out our piece, on Web Application Firewalls Vs Network Firewall.
How to find the right firewall for your business
When trying to find the best firewall to protect your business, start by defining your network firewall security plan and highlight your specific security concerns. If you are concerned with the data leaving your network in addition to incoming security, invest in a two-way firewall instead of a one-way firewall.
If you cannot afford processing slowdowns or reduced transaction speeds, you may want to consider an on-premise vs cloud-based firewall. If you don’t have in-house IT expertise, consider a hosted or cloud-based firewall solution. A company that deals with sensitive information, such as health care or payment processing, should invest in the best NGFW you can find in addition to software firewalls.
Once you have a grasp on what kind of security you need, you can use other businesses’ experiences with various products to get a sense of what firewalls would work best for you.
Examining reviews from companies of a similar size and industry as will help you consolidate the list of possible options for further investigation. By investing in the right kind of network firewall security, you can reduce the cost and impact of cybercrime on your company. If you are looking for firewall software for small businesses, we even have a piece written specifically for you. Check out the Best Firewall Software for Small Businesses.
Was this helpful?

Explore the best Firewall Software and read reviews here
